- Event Id 4776 Microsoft Authentication Package V1 From Mac Pro
- Microsoft Authentication Package
- Event Id 4776 Microsoft Authentication Package V1 From Mac To Windows 10
- Event Id 4776 Microsoft Authentication Package V1 From Mac Pro
| title | description | ms.pagetype | ms.prod | ms.mktglfcycl | ms.sitesec | ms.localizationpriority | author | ms.date | ms.reviewer | manager | ms.author |
|---|---|---|---|---|---|---|---|---|---|---|---|
4776(S, F) The computer attempted to validate the credentials for an account. (Windows 10) | Describes security event 4776(S, F) The computer attempted to validate the credentials for an account. | w10 | library | dansimp | dansimp |
- Authentication Package Type = UnicodeString: the name of Authentication Package which was used for credential validation. It is always “ MICROSOFTAUTHENTICATIONPACKAGEV10 ” for 4776 event. Note Authentication package is a DLL that encapsulates the authentication logic used to determine whether to permit a user to log on.
- Feb 12, 2017 The administrator account is set to NOT lockout.Via event viewer:PackageName MICROSOFTAUTHENTICATIONPACKAGEV10 TargetUserName ADMINISTRATOR Workstation Status 0xc000006a So. Audit failure 4776, blank workstation - IT Security - Spiceworks.
For Kerberos authentication see event 4768, 4769 and 4771. This event is also logged on member servers and workstations when someone attempts to logon with a local account. Authentication Package: Always 'MICROSOFTAUTHENTICATIONPACKAGEV10' Logon Account: name of the account Source Workstation: computer name where logon attempt originated.
Applies to
- Windows 10
- Windows Server 2016
Subcategory:Audit Credential Validation
Event Description:
This event generates every time that a credential validation occurs using NTLM authentication.
This event occurs only on the computer that is authoritative for the provided credentials. For domain accounts, the domain controller is authoritative. For local accounts, the local computer is authoritative.
It shows successful and unsuccessful credential validation attempts.
It shows only the computer name (Source Workstation) from which the authentication attempt was performed (authentication source). For example, if you authenticate from CLIENT-1 to SERVER-1 using a domain account you will see CLIENT-1 in the Source Workstation field. Information about the destination computer (SERVER-1) is not presented in this event.
If a credential validation attempt fails, you will see a Failure event with Error Code parameter value not equal to “0x0”.
The main advantage of this event is that on domain controllers you can see all authentication attempts for domain accounts when NTLM authentication was used.
Microsoft office 2011 for mac product key finder. For monitoring local account logon attempts, it is better to use event “4624: An account was successfully logged on” because it contains more details and is more informative.
This event also generates when a workstation unlock event occurs.
This event does not generate when a domain account logs on locally to a domain controller.
Note For recommendations, see Security Monitoring Recommendations for this event.
Event XML:
Required Server Roles: no specific requirements.
Minimum OS Version: Windows Server 2008, Windows Vista.
Event Versions: 0.
Field Descriptions:
- Authentication Package [Type = UnicodeString]: the name of Authentication Package which was used for credential validation. It is always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0” for 4776 event.
NoteAuthentication package is a DLL that encapsulates the authentication logic used to determine whether to permit a user to log on. Local Security Authority (LSA) authenticates a user logon by sending the request to an authentication package. The authentication package then examines the logon information and either authenticates or rejects the user logon attempt.
Logon Account [Type = UnicodeString]: the name of the account that had its credentials validated by the Authentication Package. Can be user name, computer account name or well-known security principal account name. Examples:
User example: dadmin
Computer account example: WIN81$
Local System account example: Local
Local Service account example: Local Service
Source Workstation [Type = UnicodeString]: the name of the computer from which the logon attempt originated.
Apa format microsoft word mac download. Writing a research or term paper in APA format? This starter template provides easy access to styles that match APA guidelines. This is an accessible template.
Error Code [Type = HexInt32]: contains error code for Failure events. For Success events this parameter has “0x0” value. The table below contains most common error codes for this event:
Event Id 4776 Microsoft Authentication Package V1 From Mac Pro
| Error Code | Description |
|---|---|
| 0xC0000064 | The username you typed does not exist. Bad username. |
| 0xC000006A | Account logon with misspelled or bad password. |
| 0xC000006D | - Generic logon failure. Some of the potential causes for this: An invalid username and/or password was used LAN Manager Authentication Level mismatch between the source and target computers. |
| 0xC000006F | Account logon outside authorized hours. |
| 0xC0000070 | Account logon from unauthorized workstation. |
| 0xC0000071 | Account logon with expired password. |
| 0xC0000072 | Account logon to account disabled by administrator. |
| 0xC0000193 | Account logon with expired account. |
| 0xC0000224 | Account logon with 'Change Password at Next Logon' flagged. |
| 0xC0000234 | Account logon with account locked. |
| 0xc0000371 | The local account store does not contain secret material for the specified account. |
| 0x0 | No errors. |
Table 1. Winlogon Error Codes.
Security Monitoring Recommendations
For 4776(S, F): The computer attempted to validate the credentials for an account.
| Type of monitoring required | Recommendation |
|---|---|
| High-value accounts: You might have high-value domain or local accounts for which you need to monitor each action. Examples of high-value accounts are database administrators, built-in local administrator account, domain administrators, service accounts, domain controller accounts and so on. | Monitor this event with the “Logon Account” that corresponds to the high-value account or accounts. |
| Anomalies or malicious actions: You might have specific requirements for detecting anomalies or monitoring potential malicious actions. For example, you might need to monitor for use of an account outside of working hours. | When you monitor for anomalies or malicious actions, use the “Logon Account” value (with other information) to monitor how or when a particular account is being used. To monitor activity of specific user accounts outside of working hours, monitor the appropriate Logon Account + Source Workstation pairs. |
| Non-active accounts: You might have non-active, disabled, or guest accounts, or other accounts that should never be used. | Monitor this event with the “Logon Account” that should never be used. |
| Account whitelist: You might have a specific whitelist of accounts that are the only ones allowed to perform actions corresponding to particular events. | If this event corresponds to a “whitelist-only” action, review the “Logon Account” for accounts that are outside the whitelist. |
| Restricted-use computers: You might have certain computers from which certain people (accounts) should not log on. | Monitor the target Source Workstation for credential validation requests from the “Logon Account” that you are concerned about. |
| Account naming conventions: Your organization might have specific naming conventions for account names. | Monitor “Logon Account” for names that don’t comply with naming conventions. |
If NTLM authentication should not be used for a specific account, monitor for that account. Don’t forget that local logon will always use NTLM authentication if an account logs on to a device where its user account is stored.
You can use this event to collect all NTLM authentication attempts in the domain, if needed. Don’t forget that local logon will always use NTLM authentication if the account logs on to a device where its user account is stored.
If a local account should be used only locally (for example, network logon or terminal services logon is not allowed), you need to monitor for all events where Source Workstation and Computer (where the event was generated and where the credentials are stored) have different values.
Consider tracking the following errors for the reasons listed:
| Error to track | What the error might indicate |
|---|---|
| User logon with misspelled or bad user account | For example, N events in the last N minutes can be an indicator of an account enumeration attack, especially relevant for highly critical accounts. |
| User logon with misspelled or bad password | For example, N events in the last N minutes can be an indicator of a brute-force password attack, especially relevant for highly critical accounts. |
| User logon outside authorized hours | Can indicate a compromised account; especially relevant for highly critical accounts. |
| User logon from unauthorized workstation | Can indicate a compromised account; especially relevant for highly critical accounts. |
| User logon to account disabled by administrator | For example, N events in last N minutes can be an indicator of an account compromise attempt, especially relevant for highly critical accounts. |
| User logon with expired account | Can indicate an account compromise attempt; especially relevant for highly critical accounts. |
| User logon with account locked | Can indicate a brute-force password attack; especially relevant for highly critical accounts. |
Applies to
- Windows 10
- Windows Server 2016
Subcategory:Audit Credential Validation
Event Description:
This event generates every time that a credential validation occurs using NTLM authentication.
This event occurs only on the computer that is authoritative for the provided credentials. For domain accounts, the domain controller is authoritative. For local accounts, the local computer is authoritative.
It shows successful and unsuccessful credential validation attempts.
It shows only the computer name (Source Workstation) from which the authentication attempt was performed (authentication source). For example, if you authenticate from CLIENT-1 to SERVER-1 using a domain account you will see CLIENT-1 in the Source Workstation field. Information about the destination computer (SERVER-1) is not presented in this event.
If a credential validation attempt fails, you will see a Failure event with Error Code parameter value not equal to “0x0”.
The main advantage of this event is that on domain controllers you can see all authentication attempts for domain accounts when NTLM authentication was used.
For monitoring local account logon attempts, it is better to use event “4624: An account was successfully logged on” because it contains more details and is more informative.
This event also generates when a workstation unlock event occurs.
This event does not generate when a domain account logs on locally to a domain controller.
Note For recommendations, see Security Monitoring Recommendations for this event.
They shouldn’t have waited until El Capitan was released to begin their work. Os x el capitan 10.11.6 download.
Event XML:
Required Server Roles: no specific requirements.
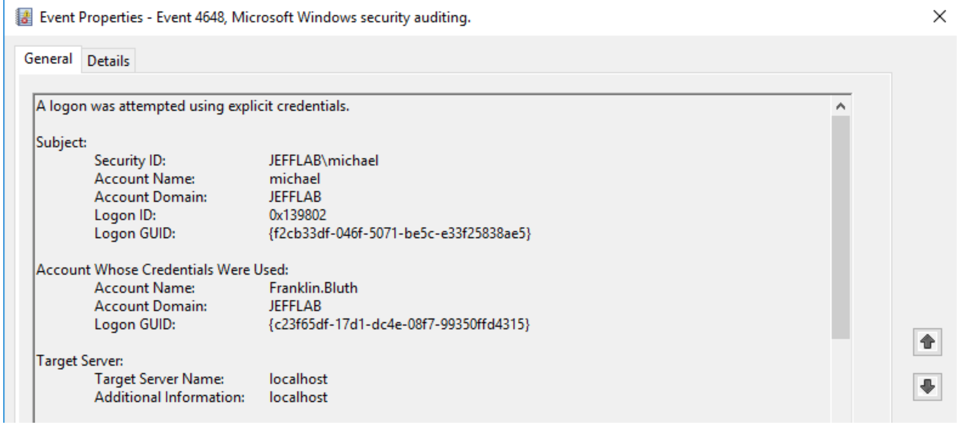
Minimum OS Version: Windows Server 2008, Windows Vista.
Event Versions: 0.
Jun 12, 2012 Word Work File D.tmp on desktop, What is it and how can I get rid of it I'm a new user of Office:mac. I discovered this evening a file on my desktop that I can't delete or get rid of. Mac microsoft word work file d location.
Field Descriptions:
- Authentication Package [Type = UnicodeString]: the name of Authentication Package which was used for credential validation. It is always “MICROSOFT_AUTHENTICATION_PACKAGE_V1_0” for 4776 event.
NoteAuthentication package is a DLL that encapsulates the authentication logic used to determine whether to permit a user to log on. Local Security Authority (LSA) authenticates a user logon by sending the request to an authentication package. The authentication package then examines the logon information and either authenticates or rejects the user logon attempt.
Logon Account [Type = UnicodeString]: the name of the account that had its credentials validated by the Authentication Package. Can be user name, computer account name or well-known security principal account name. Examples:
User example: dadmin
Computer account example: WIN81$
Local System account example: Local
Local Service account example: Local Service
Source Workstation [Type = UnicodeString]: the name of the computer from which the logon attempt originated.
Error Code [Type = HexInt32]: contains error code for Failure events. For Success events this parameter has “0x0” value. The table below contains most common error codes for this event:
| Error Code | Description |
|---|---|
| 0xC0000064 | The username you typed does not exist. Bad username. |
| 0xC000006A | Account logon with misspelled or bad password. |
| 0xC000006D | - Generic logon failure. Some of the potential causes for this: An invalid username and/or password was used LAN Manager Authentication Level mismatch between the source and target computers. |
| 0xC000006F | Account logon outside authorized hours. |
| 0xC0000070 | Account logon from unauthorized workstation. |
| 0xC0000071 | Account logon with expired password. |
| 0xC0000072 | Account logon to account disabled by administrator. |
| 0xC0000193 | Account logon with expired account. |
| 0xC0000224 | Account logon with 'Change Password at Next Logon' flagged. |
| 0xC0000234 | Account logon with account locked. |
| 0xc0000371 | The local account store does not contain secret material for the specified account. |
| 0x0 | No errors. |
Table 1. Winlogon Error Codes.
Microsoft Authentication Package
Security Monitoring Recommendations
Event Id 4776 Microsoft Authentication Package V1 From Mac To Windows 10
For 4776(S, F): The computer attempted to validate the credentials for an account.
Event Id 4776 Microsoft Authentication Package V1 From Mac Pro
| Type of monitoring required | Recommendation |
|---|---|
| High-value accounts: You might have high-value domain or local accounts for which you need to monitor each action. Examples of high-value accounts are database administrators, built-in local administrator account, domain administrators, service accounts, domain controller accounts and so on. | Monitor this event with the “Logon Account” that corresponds to the high-value account or accounts. |
| Anomalies or malicious actions: You might have specific requirements for detecting anomalies or monitoring potential malicious actions. For example, you might need to monitor for use of an account outside of working hours. | When you monitor for anomalies or malicious actions, use the “Logon Account” value (with other information) to monitor how or when a particular account is being used. To monitor activity of specific user accounts outside of working hours, monitor the appropriate Logon Account + Source Workstation pairs. |
| Non-active accounts: You might have non-active, disabled, or guest accounts, or other accounts that should never be used. | Monitor this event with the “Logon Account” that should never be used. |
| Account whitelist: You might have a specific whitelist of accounts that are the only ones allowed to perform actions corresponding to particular events. | If this event corresponds to a “whitelist-only” action, review the “Logon Account” for accounts that are outside the whitelist. |
| Restricted-use computers: You might have certain computers from which certain people (accounts) should not log on. | Monitor the target Source Workstation for credential validation requests from the “Logon Account” that you are concerned about. |
| Account naming conventions: Your organization might have specific naming conventions for account names. | Monitor “Logon Account” for names that don’t comply with naming conventions. |
If NTLM authentication should not be used for a specific account, monitor for that account. Don’t forget that local logon will always use NTLM authentication if an account logs on to a device where its user account is stored.
You can use this event to collect all NTLM authentication attempts in the domain, if needed. Don’t forget that local logon will always use NTLM authentication if the account logs on to a device where its user account is stored.
If a local account should be used only locally (for example, network logon or terminal services logon is not allowed), you need to monitor for all events where Source Workstation and Computer (where the event was generated and where the credentials are stored) have different values.
Consider tracking the following errors for the reasons listed:
| Error to track | What the error might indicate |
|---|---|
| User logon with misspelled or bad user account | For example, N events in the last N minutes can be an indicator of an account enumeration attack, especially relevant for highly critical accounts. |
| User logon with misspelled or bad password | For example, N events in the last N minutes can be an indicator of a brute-force password attack, especially relevant for highly critical accounts. |
| User logon outside authorized hours | Can indicate a compromised account; especially relevant for highly critical accounts. |
| User logon from unauthorized workstation | Can indicate a compromised account; especially relevant for highly critical accounts. |
| User logon to account disabled by administrator | For example, N events in last N minutes can be an indicator of an account compromise attempt, especially relevant for highly critical accounts. |
| User logon with expired account | Can indicate an account compromise attempt; especially relevant for highly critical accounts. |
| User logon with account locked | Can indicate a brute-force password attack; especially relevant for highly critical accounts. |